Updated October 3rd 2022
Introduction
ProxyNotShell is a post-authentication vulnerability. An attacker will require “privileges that provide basic user capabilities”.
Microsoft has confirmed the recent reports of two zero-day vulnerabilities in Microsoft Exchange Server (on-premises).
The first vulnerability in the report is CVE-2022-41040 and is a Server-Side Request Forgery (SSRF) vulnerability. The second is CVE-2022-41082 which allows Remote Code Execution when PowerShell Remoting is exposed.
Microsoft is aware of “limited targeted attacks using the two vulnerabilities to get into users’ systems”.
As usual, security researcher and former Microsoft employee Kevin Beaumont (@GossiTheDog) is on top of this one and has released his own investigation. Kevin named the vulnerability ‘ProxyNotShell’.
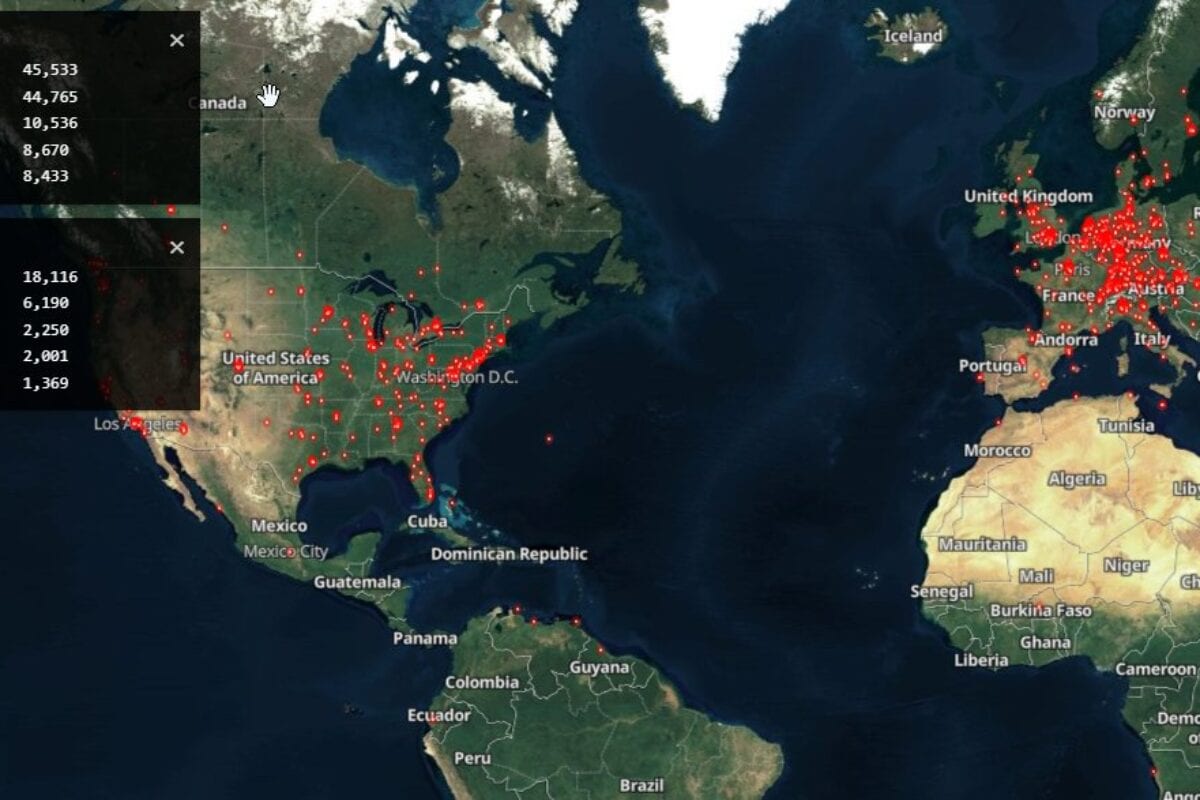
Kevin used Shodan.io to identify vulnerable versions of Exchange exposed to the internet:
https://twitter.com/GossiTheDog/status/1575774087963623426/
Mitigations
According to Microsoft: “Microsoft Exchange Online has detections and mitigations to protect customers.”
Microsoft’s proposed mitigations for on-premises installation have been bypassed as they were apparently too specific. Instead the following URL block in IIS Manager is designed to cover a wider set of attacks:
.*autodiscover\.json.*Powershell.*
We patiently await patches from Microsoft to fix these two CVE’s.