Operational Technology (OT) networks are no longer isolated. In a world where everything is connected and automated, the flawless integration between OT and IT is crucial. Why? Because it reduces costs and guarantees a higher productivity and performance. Unfortunately it also exposes your systems to new risks and threats. Industries can no longer rely on physical protection layers only. Think about the catastrophical impact of malware like Triton (2017), which made it possible for hackers to remotely take over and reprogram systems. How can you protect yourself against those attacks?
IT versus OT
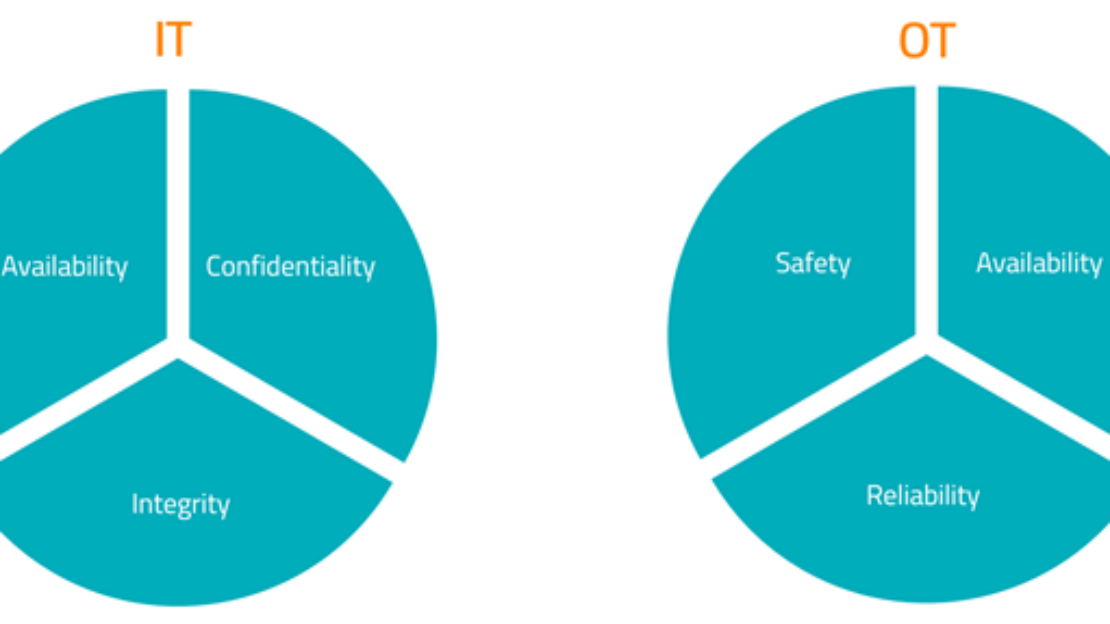
Let’s start by investigating the differences between IT and OT. In an IT environment everything revolves around the confidential handling of data and information. That’s not the case for OT systems. The impact of (temporary) damage is much bigger: it can be harmful for humans, nature and everything around it!
That’s exactly why interenational frameworks like ISO-27001, ISO-27002 and ETSI insufficiently protect an OT environment. Even the classic CIA model (Confidentiality, Integrity and Availability), THE standard for cybersecurity, provides other priorities for an OT environment. It makes sense that OT’s top priority is availability. Imagine what would happen if we have to turn off an entire production line to install a few simple updates.
This calls for a new approach: the ARS model (Availability, Reliability and Safety). We already discussed the importance of availability, but reliability and safety are just as important for OT environments. R&D data has to be protected and reliable to guarantee product quality. Finally, an industrial company needs to be able to guarantee safety to employees, customers and the environment.
Want to know more about OT security?
That was a first, short introduction to OT security. Check out part 2 to learn more about the OT framework and in-depth defense. Questions about the above? Don’t hesitate to contact us!



