Cybersecurity and connectivity are more than ever a crucial duo at the heart of our digital society. Companies that want to grow further digitally are therefore strongly committed to these two essential pillars. But they need to take into account a number of irreversible trends and serious challenges. Just think of the unprecedented possibilities of Generative AI in the fight against cyber threats as well as the constantly evolving risks that our hyper-connected world entails. At spotit we naturally follow these developments closely. Not only research and consultancy firm Gartner has a clear view on this. We also asked ‘our’ chatGPT Wim Remes, Head of Operations, to share his insights as well.
What does Gartner say?
We will see many significant transformations in both cybersecurity and connectivity in 2024. As companies worldwide try to adapt to these changes, understanding the most important trends is crucial to stay ahead. Viewed through the lens of Gartner, the following five trends and insights are put forward:
1/ The rise of Artificial Intelligence in Cybersecurity
The use of Artificial Intelligence (AI) in cybersecurity is a game changer. AI algorithms are becoming increasingly sophisticated, able to detect and respond to threats faster than humanly possible. This trend is not just about defense, but also about predictive analytics – identifying potential vulnerabilities before they can be exploited.
2/ The Evolution of Edge Computing
Edge computing revolutionizes connectivity by processing data closer to the source. This shift reduces latency, increases speed and improves reliability. However, it also presents new cybersecurity challenges. Protecting the wide variety of devices and data points at the “edge” requires innovative security approaches.
3/ Zero Trust security models
The concept of “never trust, always verify” is a cornerstone of cybersecurity strategies. As working from home blurs the boundaries of traditional network perimeters, zero trust models ensure that security is not dependent on location, but on continuous verification of identity and access privileges.
4/ The expansion of 5G
The rollout of 5G networks makes ultra-high bandwidth connectivity ubiquitous, enabling an explosion of connected devices and applications. However, this expansion also opens up new avenues for cyber attacks. Ensuring the security of 5G networks and connected devices is paramount to unleashing their full potential without compromising security.
5/ Regulations and privacy
With the increasing frequency of data breaches, governments worldwide are imposing stricter data protection regulations. Companies must navigate this complex regulatory landscape, ensuring compliance to avoid hefty fines and reputational damage, while also protecting customer privacy. The recent NIS2 Directive is a concrete application of this and obliges companies and organizations to invest more in cyber security. Read more about NIS2 here.
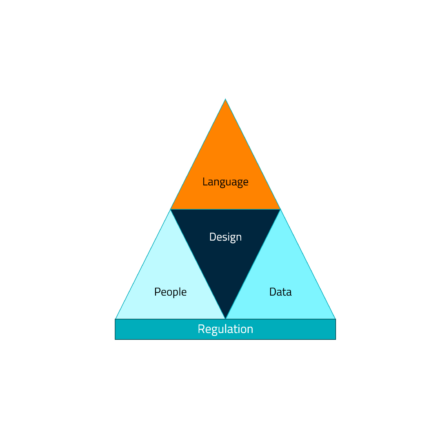
Feet on the ground
Wim Remes, Head of Operations at spotit, naturally agrees with the trends put forward by Gartner. At the same time, he calls for the necessary sobriety. His advice: start by getting the basics right and grow step-by-step in digital maturity, with the necessary attention to first-class connectivity and increased cybersecurity in every phase. Sounds simple, but it isn’t always that easy. Wim mentions the following challenges:
1/ Language
Management and IT still too often speak different languages. Ensuring that they understand each other – ‘standardizing’ that language – is an important challenge so that the right information goes to the right people. Especially now that regulations such as NIS2 ensure that management can be held liable, it is necessary that clear and plain language is spoken.
2/ People
Technologies are a necessity and a useful tool, but people make the real difference. People with certain expertise and accumulated experience know how to act at critical moments. Ensure that people remain trained by, for example, regularly organizing table-top exercises. With this accumulated experience and expertise, incidents are handled in a smooth and structured manner, everyone knows their place in major incidents, and no essential time is lost. Of course, teamwork is crucial here. Ensuring that everyone is attuned to each other is a challenge that should not be underestimated.
3/ Design
Today, the design of IT infrastructure must be ‘Distributed’, ‘Immutable’ and ‘Ephemeral’. Many separate components must be able to work together. Changes in a system must be detectable and monitored. Finally, we must also ensure that entire infrastructures, or their components, can be renewed easily and in a controlled manner. This feature allows us to continue operations with a reliable infrastructure at the first indications of a cyber incident. This architectural transformation has not yet (fully) dawned on many people today.
4/ Data
Data is a very big challenge for many organizations. After all, data is increasingly distributed and is increasing enormously. How and where do you store that data and how do you make sense of that data? For example in Security Operations. Here we see an evolution towards a ‘data pipeline’. A data pipeline is a series of processes that moves and transforms data from one location (the source) to another (the target). It is a crucial part of data engineering and is often used in the context of big data, where large amounts of data need to be processed and analyzed continuously.
5/ Regulations
New legislations such as NIS2 and DORA (for the financial world) are coming our way. Approach this pragmatically. At NIS2, Third Party Security Management – identifying your most important and critical suppliers – becomes the most important challenge. Make sure you have control over this process and work with these partners to secure the supply chain together.
Watch Wim’s full recorded session:
Would you like to schedule a sparring session with Wim about the above mentioned challenges regarding cybersecurity and connectivity? Contact Wim now!



